Following is an abstract of our White Paper regarding container technologies for HPC.
Download the complete document here.

Introduction
Container technologies have revolutionized software deployment and management, providing portability, scalability, and reproducibility across various computing platforms. While containers have gained significant popularity in diverse domains, their adoption in high-performance computing (HPC) environments poses unique challenges. In this article, I conduct a short evaluation of container technologies with a specific focus on their suitability for HPC systems. This analysis considers performance, security vulnerabilities and adherence to OCI standards as key factors influencing container technology selection.
Docker: The Pioneering Container Technology
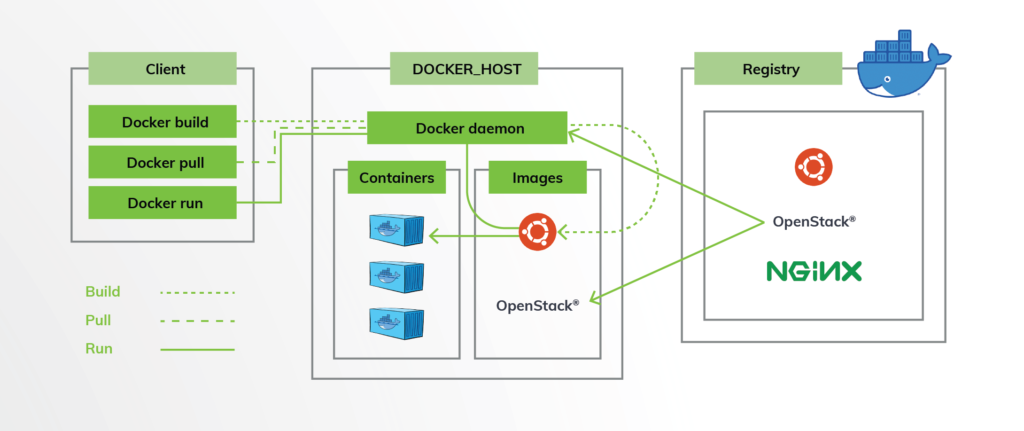
Let’s start with Docker, the pioneering container technology that has propelled the container revolution. Docker’s architecture, centered around a root-owned daemon, offers advanced features but introduces limitations for HPC use cases. Vulnerabilities to privilege escalation, integration challenges with workload managers, and difficulties in running in rootless mode make Docker less suitable for HPC environments. Nonetheless, its extensive adoption in non-HPC settings provides a valuable reference point for evaluating other container technologies.
Singularity: Optimized for HPC
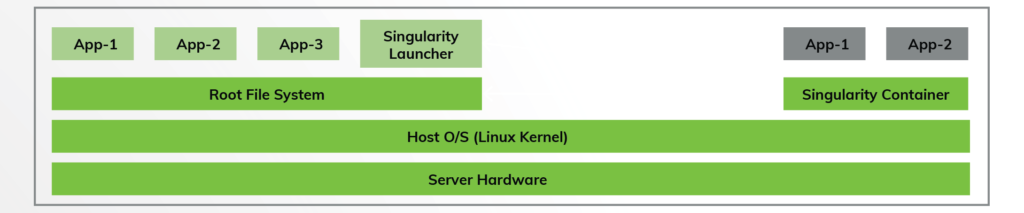
Singularity is a container technology designed specifically for HPC environments. Singularity offers strong reproducibility features, seamless integration with workload managers, and support for specialized HPC resources like GPUs and parallel file systems. It enables accessibility for unprivileged users and provides limited full rootless mode for enhanced security. However, limitations include limited interoperability with OCI standards and potential fragmentation between different forks, affecting feature availability and performance. Despite these challenges, Singularity remains popular within the HPC community due to its specific optimizations for scientific workloads.
Apptainer: Advancing Security and Performance
Singularity was renamed Apptainer, when it joined the Linux Foundation project, with the aim of operating entirely in unprivileged mode using user namespaces. By eliminating the need for setuid binaries, Apptainer addresses security vulnerabilities while maintaining performance. It builds upon Singularity’s strengths and seeks to overcome some of its limitations.
Apptainer’s primary focus is on enhancing security within HPC environments. By running in unprivileged mode, it significantly reduces the attack surface and minimizes the risk of privilege escalation. This approach aligns with the security requirements of many research institutions and ensures that containerized applications can be executed safely. Furthermore, Apptainer’s commitment to being fully open-source and community-driven further instills confidence in its security practices.
Apptainer leverages user namespaces to avoid the overhead of running containers as root, resulting in improved performance for containerized applications. By eliminating the need for root privileges, Apptainer ensures that HPC workloads can benefit from the full capabilities of the underlying hardware while maintaining a high level of security.
Although still in its early stages, Apptainer shows promise in addressing the security concerns associated with Singularity. By providing a secure and performant container environment, Apptainer aims to become a go-to choice for HPC workloads that require a balance between security and performance. Continued development and community support will be crucial for its growth and adoption within the HPC community.
Apptainer evolves and matures, it has the potential to carve out its own niche by offering advanced security features and optimized performance for HPC environments.
Podman: Lightweight Alternative
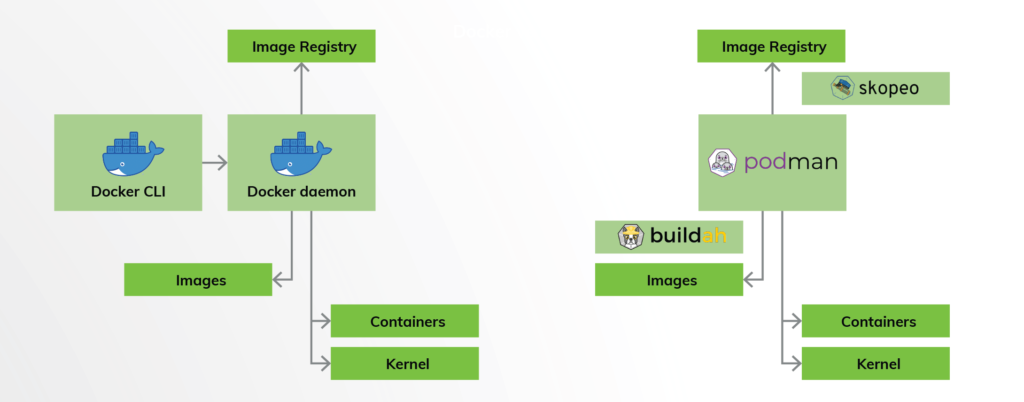
Developed by Red Hat, Podman emerges as a lightweight alternative to Docker. Operating without a daemon, Podman eliminates the need for a root-owned process. It offers a full rootless mode, enabling unprivileged users to perform most container operations. Additional tools like skopeo and buildah enhance its capabilities. However, the use of user namespaces affects performance, and compatibility with NFS home directories is limited. Nevertheless, Podman’s simplified architecture and improved security make it an attractive choice for HPC environments prioritizing security and isolation over performance.
Sarus: Balancing Standards and Optimization
Sarus, developed by CSCS, focuses on HPC environments while adhering to OCI standards. It employs a root-owned setuid binary and delegates image building to external tools like Docker. Sarus allows container customization through hooks and demonstrates compatibility with various container registries. However, it lacks built-in image-building functionality and requires manual synchronization of user information. Sarus strikes a balance between Singularity’s HPC optimizations and Docker’s broader ecosystem compatibility, making it a viable choice for HPC environments with specific requirements.

Comparison and Evaluation
In comparing these container technologies for HPC environments, several key aspects come into play. Docker, despite its widespread use, faces challenges related to security vulnerabilities and integration with HPC workflows. Singularity and Apptainer excel in addressing HPC requirements and security concerns, but interoperability limitations and potential fragmentation may impact their widespread adoption. Podman offers a lightweight and secure alternative, although performance considerations and compatibility with certain setups should be taken into account. Sarus strikes a balance between optimization and standards adherence. System administrators and researchers in the HPC domain can leverage these findings to make informed decisions when selecting container technologies.
Conclusion
In conclusion, the evaluation of container technologies for HPC environments is a dynamic process as advancements continue. Docker, Singularity, Apptainer, Podman, and Sarus offer unique features and considerations. Through a comprehensive understanding of their performance, security, integration capabilities, and adherence to standards, organizations can make informed decisions to optimize resource utilization and meet the demanding requirements of HPC. Ongoing research and experimentation are essential to stay updated with the evolving landscape, enabling the adoption of container technologies that enhance productivity, scalability, and reproducibility in HPC workflows.